OAuth URLs
Patient
Authorize: https://patient-api.docsink.com/oauth/authorizeToken: https://dev-apps.docsink.com/oauth/token
Staff
Authorize: https://apps.docsink.com/oauth/authorizeToken: https://apps.docsink.com/oauth/token
Accessing any of DocsInk services requires an access token to be present in the Authorization header of the HTTP request.
System level access tokens granting administrator like permissions when using the APIs. All bot tokens issued are directly tied to a specific DocsInk organization. Bot tokens are ideal for integrations that operate in the background and require no user interaction. These tokens get generated when an administrator of an organization has installed your client application into their account.
Bot tokens are disabled by default. To enable, navigate to the "Bots" section within your client application settings and click the checkbox to active the bot user. When activated, you'll see a section at the bottom of the page title "Bot Tokens". This will show you a list of bot tokens for each organization that has installed your client application. A new event is triggered when an organization installs your application. The event will be posted to the registered events callback url with the payload containing both the organization id and access token of the bot.
It is in our roadmap to support the client credentials grant type in the near future. This will allow us to set expirations for bot tokens and generate them on the fly as-needed using the client application's id and secret.
User permissioned access tokens that provide API interactions in the context of a specific user. These are ideal when you want initiate actions on behalf of a user. For example, cancelling an appointment as a patient or a provider approving device orders.
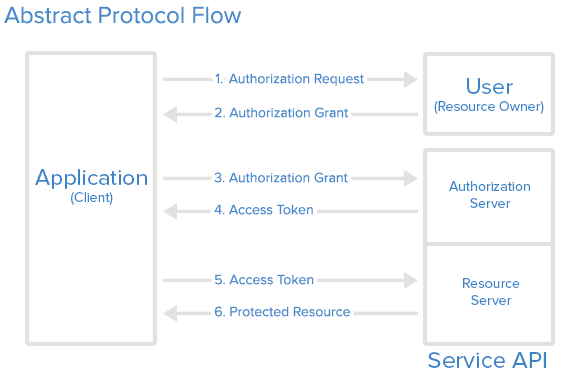
User access tokens are obtained using the OAuth2 Authorization Code flow. Your application can also leverage this flow to provide a seamless single sign on experience. If the organization installing the bot is also integrated with an external Identity Provider (e.g. customer Active Directory), the users will be able to login with their existing enterprise credentials.